- This video doorbell camera has just as many features are my Ring - and no subscription required
- LG is giving away free 27-inch gaming monitors, but this is the last day to grab one
- I tested this Eufy security camera and can't go back to grainy night vision
- I replaced my iPhone with a premium dumbphone - here's my verdict after a month
- Build your toolkit with the 10 DIY gadgets every dad should have
ICS/OT Cybersecurity 2022 TXOne Annual Report Insights

Cyber Threats
This article gives an in-depth overview of TXOne’s insight report on ICS/OT cyber incidents.
Read time: ( words)
TXOne Networks, Trend Micro’s dedicated OT security subsidiary, has released its annual ICS/OT security report. This report consists of three studies: insights from ICS/OT cyber incidents, an analysis of the ICS/OT security market, and an online survey of asset owners. This blog post presents the essence of the report.
ICS/OT Incidents in 2022
TXOne’s research team monitors cybercrimes and malicious activity in cyberspace and has tallied the number of attacks and incidents they saw in 2022.
Ransomware Attacks the Industries
Ransomware-as-a-Service (RaaS) continues to adopt the multiple extortion model. In the latter half of 2022, we began to see a surge in RaaS criminal groups like Black Basta and Pandora. But that was just the start. LockBit 3.0 took things up another notch with its malicious cyber tactics, from data destruction to ransom demands, even offering stolen information for sale on shady dark websites.
No industry was safe – smart manufacturing, energy, and food & agriculture were all affected, as well as healthcare & public health, which saw an increased rate of cyberattacks after the release of this notorious program.
In addition, Ransomware is constantly evolving, utilizing sophisticated techniques to evade analysis. For instance, programs like Egregor and LockBit 3.0 require a secret parameter for researchers to begin studying the malicious code. And it uses advanced encryption tactics like intermittent encoding in small chunks to reduce the intensity of file I/O operations and avoid statistical analysis and detection.
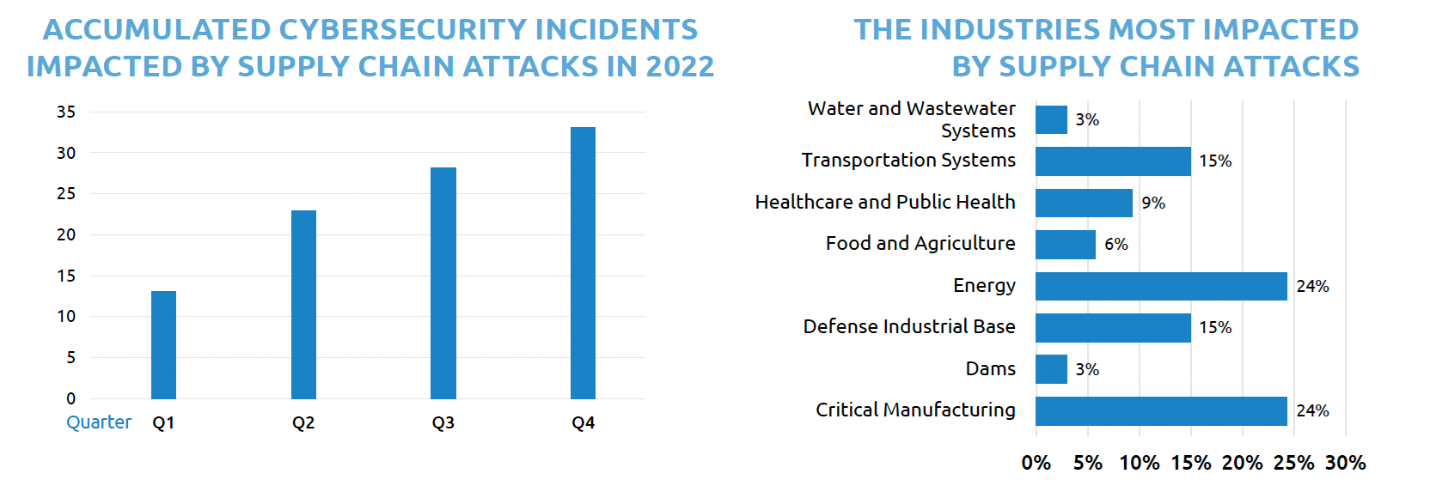
In 2022, supply chain attacks on major sectors skyrocketed. Energy and Critical Manufacturing industries face an exceptionally high risk of supply chain attack. Of the supply chain attacks TXOne grasped in 2022, 24% were in the energy sector and 24% in critical manufacturing. Automotive factories made up most of them due to automation growth in this area. The energy sector is escalating risk due to threats from geopolitical conflicts and the vulnerability of interdependencies with other sectors.
OT Security Market Driving Forces
TXOne conducted a study to interview asset owners and related stakeholders in the United States, Germany, and Japan to find out how each industry is progressing in OT security and understand the current problems and causes in a changing environment.
Typically, a successful digital transformation in the industry begins by identifying key application cases, and then implementing them on a small scale in factories. The report suggested some examples.
- Energy sector: IT and OT teams can remotely access operational data to help industries (such as power grids, oil, and gas) optimize preventive maintenance of industrial control equipment, perform damage assessments, and handle inventory monitoring, or optimize energy distribution.
- Manufacturing sector: IT and OT teams can use automated material transfer systems and robotic arms for automated production, adjust production processes in real-time, improve production efficiency, and reduce manufacturing costs and waste. For example, data analysis can be used to reduce electricity costs or reduce redundant inventory.
The report also summarizes cyber security regulations and government trends in each country.
The OT Security End User Survey
TXOne Networks commissioned Frost and Sullivan to conduct a global survey on the current state of OT/ICS cybersecurity in the manufacturing industry. The study interviewed decision makers or leaders in advanced manufacturing countries such as the United States, Japan, and Germany, involving 300 OT/ICS stakeholders.
Three major verticals were surveyed, dividing the subjects with roughly equivalent sample sizes. 34% were from general manufacturing, 33% were from automotive manufacturing, and 33% were from pharmaceutical manufacturing.
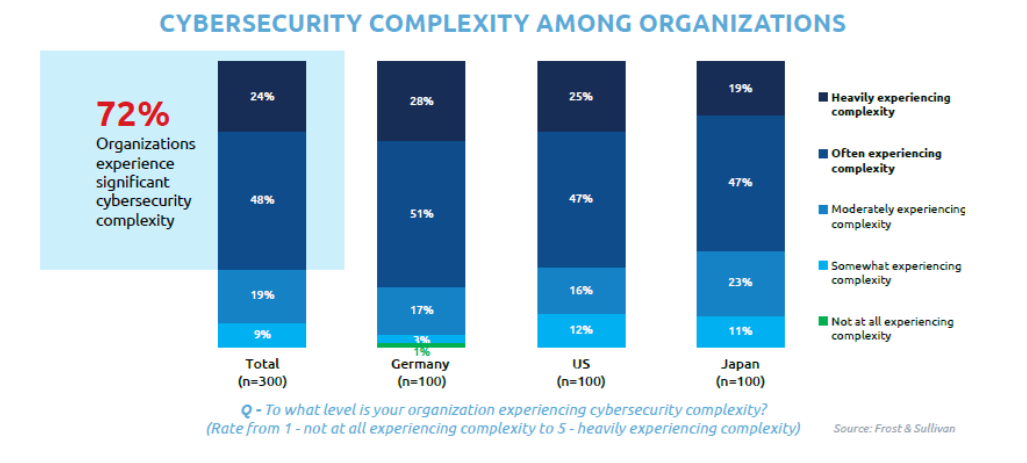
Organizations face various security risks, and this survey explores decision-makers current views on the topic. It digs deeper to uncover their challenges while measuring their vulnerability and resilience levels.Some of the findings are below:
- 72% of organizations face cybersecurity complexity. (24%: heavily experiencing complexity, 48%: often experiencing complexity)
- The top type of IT incident experienced was APT attack (33%), and the top type of OT incident experienced was phishing emails aimed to penetrate systems (37%).
- The top source of OT incidents is new assets containing vulnerability/malicious files by default (47%)
- Organizations have already been using solutions for OT security (93%), planning improvements (85%), and increasing adoption with spending on OT security (76%)
Most asset owners understand the difference between enterprise IT and ICS/OT environments. The evaluation for choosing a cybersecurity solution can be divided into three aspects.
- Strategic aspect: Overall, aggregate quality is the most important strategic capability for enterprises
- Operational aspect: The ability to integrate with other applications and technologies is the most important operational function for any organization
- Performance aspect: Organizations should focus on performance and availability to drive business outcomes.
Download the full report from TXOne’s web to learn more about the ICS/OT cybersecurity environment in 2022.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

